cs471:cs_471_-_virtualization_and_containers
Table of Contents
Virtualization and Containers
Hypervisor Virtualization
- Virtualization software on a host computer creates virtual hardware on which an OS file system image is installed and run (a guest OS).
- The hypervisor (AKA “virtual machine monitor”)
- Software layer that mediates between virtual machines (VMs) and the underlying hardware on which they run.
- Responsible for sharing system resources among the guest operating systems
- Guest OSes are isolated from one another, and access the hardware exclusively through the hypervisor.
- Full virtualization
- Emulate an entire computer in software only
- Guest OSes run unmodified on the simulated computer and don't “know” they are being virtualized.
- Example: QEMU
- Paravirtualization
- Guest OSes are modified to cooperate with a hypervisor, gaining performance benefits over full virtualization.
- Modified guests “know” that they are running virtualized and cooperate actively with the hypervisor.
- Example: Xen
- Hardware-assisted virtualization
- Intel and AMD CPUs contain features (Intel VT and AMD-V) that accelerate virtualization.
- “accelerated virtualization”
- Access to CPU virtualization instructions controlled by hypervisor
- Guest OSes need not “know” that they are being virtualized to gain performance benefits.
- Benefits both full- and paravirtualization
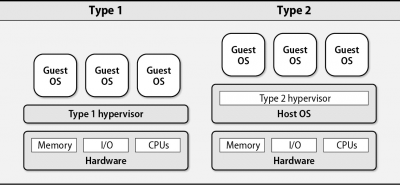
- Type 1 vs Type 2 hypervisors
- Type 1 hypervisors run directly on the hardware without a supporting OS.
- “bare-metal” or native hypervisor
- Examples: VMware ESXi, XenServer
- Type 2 hypervisors are userspace applications that run on top of another general-purpose OS.
- Examples: KVM, QEMU, Workstation-oriented virtualization packages such as Oracle’s VirtualBox and VMware Workstation and Parallels
Containers
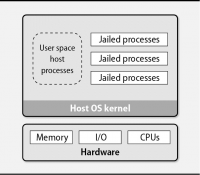
- Containerization
- Different approach to guest OS isolation that does not use a hypervisor
- Relies on kernel features that isolate processes from the rest of the system.
- Each process “container” or “jail” has a private root filesystem and process namespace.
- Contained processes share the kernel and other services of the host OS, but they cannot access files or resources outside of their containers.
- Containers do not require virtualization of the hardware
- Low resource overhead
- Most container implementations offer near-native performance.
Comparison of Virtual Machines and Containers
cs471/cs_471_-_virtualization_and_containers.txt · Last modified: by jchung