cs471:cs_471_-_introduction_unix_installation
Table of Contents
Introduction, Installation
Introduction, Discussion of Course Content
What is a [UNIX System] Administrator?
Noun:
1. One who administers; one who manages, carries on, or directs the affairs of any establishment or institution.
2. One who has the faculty of managing or organizing.
3. One who executes or performs the official duties of religion, justice, etc.; one who dispenses or ministers to the public in such matters.
4. One to whom authority is given to manage estates, etc. for the legal owner during his minority, incapacity, etc.; a trustee, a steward. esp. in Sc. Law. `A person legally empowered to act for another whom the law presumes incapable of acting for himself' (Encyc.Brit.), as the father of children under age.
System Administration Tasks
- Any task that cannot be completed without administrator privileges
- Any task that requires writing to privileged system directories
- Exceptions are global temporary directories, such as /tmp in UNIX, which any user can usually write to
Some Common System Administration Tasks
- Performing backups
- Adding and removing users
- Adding and removing hardware
- Restoring files from backups that users have accidentally deleted
- Installing new OSes and software
- Answering users' questions
- Monitoring system activity, disc use and log files
- Monitoring system security
- Adding new systems to the network
- Talking with vendors to determine if a problem is yours or theirs, and getting them to fix it when it is their problem
- Figuring out why “the network” (or “email”, or “the computer”) is “so slow”
- Trying to free up disc space
- Rebooting the system after a crash (can happen at any time)
- Using management software and/or writing scripts to automate as many of the above tasks as possible
Types of Users
- administrator/root (a.k.a. “super user”–guard this account!)
- normal users
- service related users
- the “nobody” or “www” user for web servers, the “ftp” user, the “mysql” user
- See /etc/passwd on UNIX/Linux
Installation
- One of the first tasks you will run into as a system administrator
- We will install a distribution of Linux in a virtualized environment.
- The system you install today will be one of the systems that you will be the administrator of this semester.
- Follow my directions carefully as we install Linux.
- This could take an hour or more.
- After a successful installation, see Linux Virtual Machine Management - Week 1.
Review of UNIX
UNIX Variants
The following URL shows a “family tree” of the UNIX operating system: http://www.levenez.com/unix/history.html
- Major UNIX variants that I've come in contact with:
- Digital UNIX 3.x/4.x (formerly OSF/1)
- Tru64 (formerly Digital UNIX 3.x/4.x)
- SunOS 5.x (Solaris 2.x, 8, 9)
- Linux 2.x
- IRIX 5.x/6.x
- HP/UX 9.x/10.x
- FreeBSD
- NetBSD
- Darwin/Mac OS X
- Most of the above contain vestiges of both SysV and BSD UNIX
- Linux is more “SysV-ish” then “BSD-ish”
- Differences between SysV and BSD
- in system init (startup)
- printing
- certain key system commands such as ps
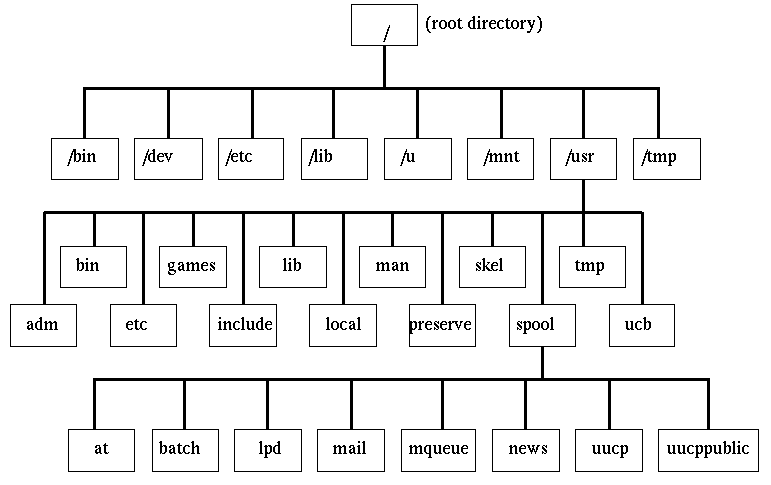
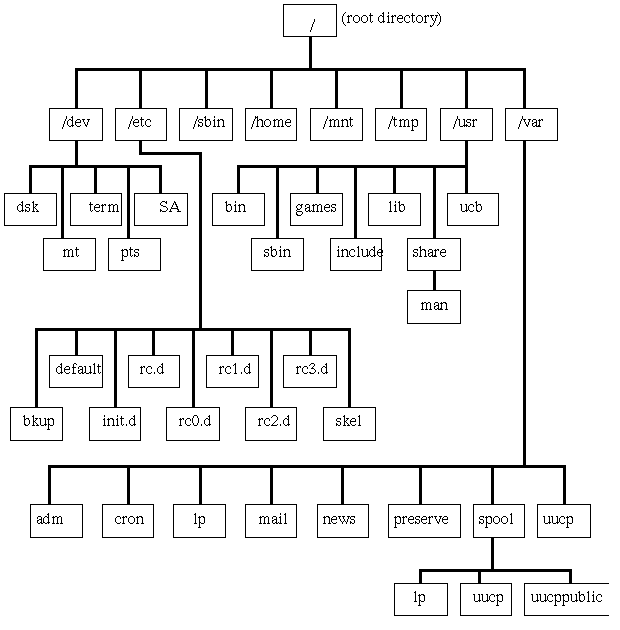
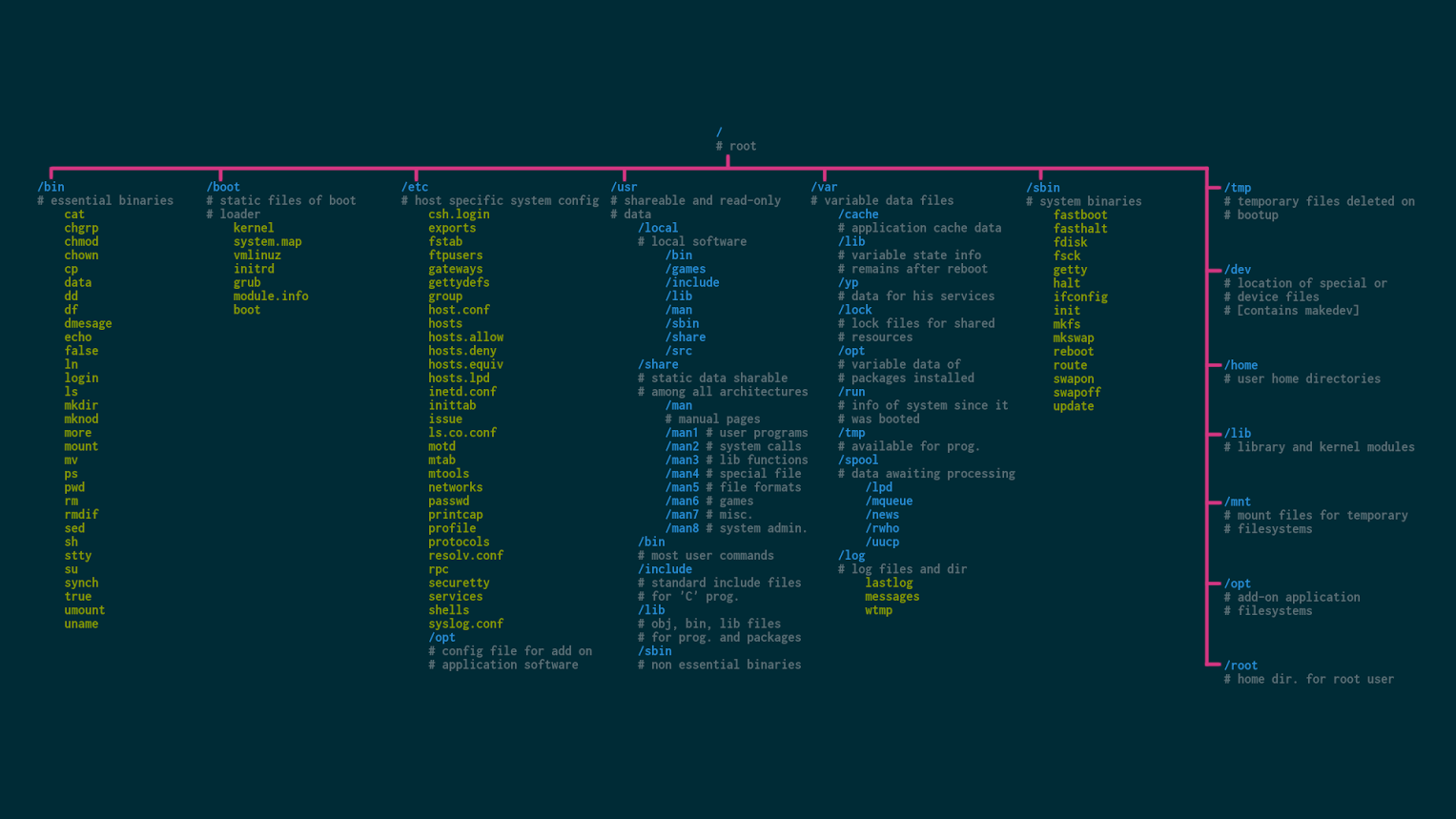
- file system hierarchies; see diagrams below
- Here is an example of the BSD file system layout:
- Here is an example of the System V.4 file system layout:
- Here is the modern Linux file system layout:
- No drive letters, e.g. C:, D:, etc.
- File systems on drives are mounted and appear as directories under the root “/” directory
- Even removable media drives, e.g. CD-ROM, usb
Tips for UNIX System Administration
- Things to be aware of when using the root account on your newly installed systems:
- Usual command prompt is $ for normal users and # for root.
- $HOME directory for root is /root on Linux and / on other versions of Unix.
- Do you know what your home directory is on the Linux lab machines and Linux servers?
- Use “good” passwords.
- Remove the current working directory (a.k.a., “.”) from your PATH.
- Never leave the terminal unattended.
- Use a terminal locking program or locking screen blanker or screen saver.
- Limit who has the root password to as few people as possible.
- Can be accomplished by limiting use of the su command to a certain group
- Don't allow ssh login as root.
- Use sudo.
- Never execute any regular user's program as root (possible Trojan Horse).
- Never let anyone else run a command as root, even if you are watching them.
- You risk having your password stolen by “sniffers” if you use internet clients like “telnet”, “ftp”, access email remotely with POP/IMAP (any network protocol involving “clear-text” passwords).
Some essential UNIX administration tools
- man
- su
- sudo
- ps
- find
- grep, egrep
- df / du
- nano, vi, emacs, or other preferred non-GUI editor
- Bash (/bin/bash), Korn Shell (/bin/ksh) or other preferred sh-compatible shell.
- cron / at
UNIX Manual Pages (man pages)
- UNIX Manual Sections
Contents BSD System V
Sections Sections
User Commands 1 1
System Calls 2 2
C and other library routines 3 3
Special files, device drivers, hardware 4 7
Configuration files 5 4
Games 6 6 or 1 or
NA
Miscellaneous commands 7 5
Administration commands 8 1M
Maintenance commands 8 8
Local commands l l
The ps command
- ps command (BSD)
Common options (commonly used w/o dash):
a print all processes involving terminals
e print environment and arguments
l long listing
u print user information
x include processes with no terminals
Meaning of user information columns:
%CPU percentage use of CPU
SZ set size (in 1024 byte pages) of the process
RSS resident set size (in pages) of the process
STAT state of the process
TIME time, including both user and system time
- ps command (System V)
Common options (commonly used w/ dash):
-e print all processes
-f print full listing
-l long listing (more info than -f)
Meaning of full listing columns:
S state
PRI priority
SZ set size (in 4096 byte pages) of the process
STIME starting time
TIME cumulative execution time
- common ps examples (Linux, which can use both SysV and BSD syntax)
$ ps aux | grep sshd # is sshd running?
$ ps fax | less # show process "tree" view
The find Command
- Syntax:
$ find starting-dir(s) matching-criteria-and-actions
Matching criteria
-atime n file was accessed n days ago
-mtime n file was modified n days ago
-size n file is exactly n 512-byte blocks
-type c file type (e.g., f=plain, d=dir)
-name nam file name (e.g., `*.c')
-user usr file's owner is usr
-perm p file's access mode is p
Actions
-print display pathname
-exec cmd execute command ({} expands to file)
- find examples
# Starting in current directory, find C source files
$ find . -name '*.c'
# Starting in root directory, find and list files that are
# more than 30 days old and >30 MB in size
$ find / -size +3M -mtime +30 -exec ls -l {} \;
Other Helpful Tools and Resources
- Usenet newsgroups … and their Frequently Asked Questions (FAQ) files (http://www.faqs.org).
- Read Usenet news at http://groups.google.com. Relevant groups are…
- comp.sys.*.admin, comp.unix.*, alt.security, comp.security.*, comp.lang.*
- Largely superceded by the Web (project sites, *stack*, blogs and other forums)
- User groups/organizations
- Usenix (http://www.usenix.org/)
- League of Professional System Administrators (http://lopsa.org)
- Local UNIX/Linux user groups
My Expectations
- Try things on the machines that you administer for this class.
- But trying different things and experimenting can lead to mistakes, so always document your changes and experiments in your journal.
- Before you go and break your machine, take the necessary precautions.
- System configuration files are in /etc; back this directory up somewhere.
- When modifying a configuration file, copy it to a backup.
- 'cp somepackage.conf somepackage.conf.original'
- When modifying a configuration file, use comments and add your signature and date of modification.
- Be careful when using 'rm'; in fact, try not to use 'rm'.
- Try to use 'mv' and 'cp' instead.
- If unsure of something, ask me.
Week 1-2 Minimum Configuration of Linux Machines
- root and normal user accounts per student
- normal user account for jchung
- password to be announced
- dhcp hostname created and active
- secure shell daemon, sshd, running (See http://www.openssh.org)
- ssh to cslab or rockhopper and ssh back
- These packages may not have been installed and are needed. Use 'apt-get install' to download and install them on your machine.
aptitude
less
links
mc
mutt
sudo
vim
vlock
wget
- See the list of mandatory CS-471 tasks.
Installing Debian Linux Packages
dpkg (see 'man dpkg')
- Debian packages have the .deb extension and can be downloaded and installed using the dpkg command.
- To install a package called foo-4.5.deb
- Example: Debian .deb packages obtained from http://www.google.com/chrome
$ dpkg -i foo-4.5.deb
- dpkg is the lowest-level package management system on Debian
- Additional dpkg commands (see 'man dpkg'):
# lists the packages installed on the system
$ dpkg -l
# remove the specified package from the system
$ dpkg --remove package
# completely remove the specified package
$ dpkg --purge package
# search for files within installed packages
$ dpkg -S nslookup
- Note: dpkg does not resolve package dependencies; will only warn if package dependencies aren't met and refuse to install the package
- Depends on admin to resolve dependencies manually
apt (see 'man apt')
- high-level package management system which acts as dpkg front end
- Most oft used command is 'apt-get' (see 'man apt-get')
- apt-get knows where to download packages and dependencies from reading /etc/apt/sources.list
- To install a package called foo version 4.5
$ apt-get install foo
- apt-get resolves package dependencies and downloads & installs packages that foo depends on
searching for packages
apt-cache search search_string- If aptitude package is installed, run aptitude search search_string
cs471/cs_471_-_introduction_unix_installation.txt · Last modified: by jchung